the paper titled "define-use guided path exploration for better forced execution" by the intelligent software security research team from our information security research laboratory has been accepted by issta 2024, a top international academic conference in the field of software engineering. the first author of the paper is he dongnan, a master's student from the class of 2023, and the supervising professor is associate professor you wei. master's student xie dongchen from the class of 2023 and doctoral student wang yujie from the class of 2021 also contributed to the publication of this paper. the work on this paper initially began as an enhancement project for the undergraduate course "software security analysis." it was later submitted to the 15th national college student information security contest "work competition," and after multiple revisions, it was submitted to and accepted by this top international academic conference. this represents an attempt at integration between teaching, competition, and research.
issta (acm sigsoft international symposium on software testing and analysis) is recognized as one of the authoritative top conferences in the field of software engineering. founded in 1992, it is recommended by the china computer federation (ccf) as an a-class conference.
title of the paper: define-use guided path exploration for better forced execution
authors: dongnan he, dongchen xie, yujie wang, wei you, bin liang, jianjun huang, wenchang shi, zhuo zhang, xiangyu zhang
corresponding author: wei you
research background:
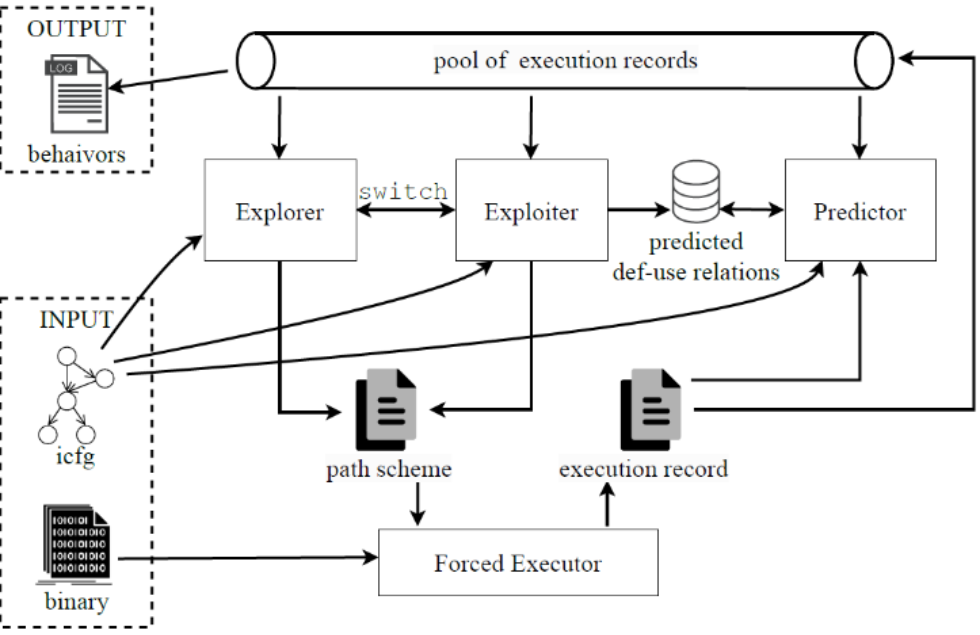
in recent years, malware has become a prominent security threat. direct dynamic execution of malware often fails to fully expose its hidden malicious behaviors. forced execution techniques, which explore program paths by forcibly setting branch conditions, are effective in circumventing malware's self-protection mechanisms and revealing its hidden malicious activities. however, current forced execution approaches have limitations in their path exploration algorithms: they change control flow without considering data flow, which may lead to missing critical data flows or triggering infeasible data flows.
abstract of the paper:
the paper introduces a prototype system named dueforce, which employs a dynamic self-supervised approach to identify define-use relationships and uses them to guide path exploration. specifically, after each execution, dueforce collects memory read-write information to predict previously undiscovered define-use relationships and corrects earlier predictions. experiments demonstrate that dueforce significantly improves the analysis results of forced execution and effectively enhances the detection of hidden malicious behaviors.
dongnan he is a master's student in the school of information at renmin university of china, specializing in information security and focusing on research areas such as binary program analysis and fuzz testing. he completed his undergraduate studies at the school of information, renmin university of china, as part of the 2019 turing class.

wei you, an associate professor in the computer science department at renmin university of china, is selected as a national young talent project awardee. he has long been engaged in the automated discovery of software vulnerabilities and the dynamic/static analysis of binary programs, uncovering nearly a hundred security vulnerabilities in common applications and exposing hundreds of suspicious behaviors in malicious applications. he has published over ten papers in top international academic conferences and journals in the fields of information security and software engineering, winning the best paper award once and being nominated for the best application security paper award twice. he was honored with the "first prize in natural science" by the china computer society. for more information, you can visit his personal webpage at https://www.youwei.site/ and his research group webpage at https://rucsesec.github.io/.




